Chesa Keane, an Associate member of Global Travelers, is a long-time consultant in many aspects of IT. As members of a virtual Rotary club, we are all, by definition, on-line to various degrees. Chesa is launching a new series to help us understand all things Internet. She starts with browser hygiene. Cookies, anyone?
You have all seen those messages that pop up when you first go onto a new website: ACCEPT COOKIES? If you just want to get on with exploring this website, you are inclined to simply Accept the cookies on the website and move on. But what are cookies and what do they do?
Definition of Cookies: Cookies are small text files that websites push to your computer and other devices used to access the Internet such as your phone or iPad. Cookies are helpful because they hold and manage the information about your visit. Cookies can contain your login details, contents of your shopping cart, as well as identify your user preferences. The intent is to make your browsing experience easier not only for the current visit but for future visits as well.

So is this a bad thing? It can be, but let’s explore the process and purpose first and you can decide how to manage these cookie monsters.
There are two types of cookies:
- First-party cookies – those cookies sent to your device by the website you are visiting.
- Third-part cookies – those cookies sent to your device by other websites, especially for advertising and tracking of behavior.
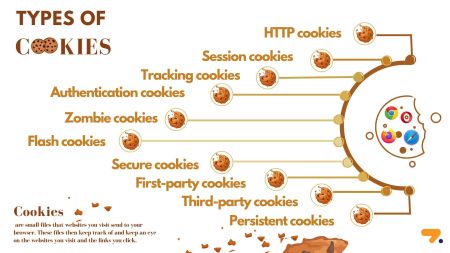
Most Common Uses of Cookies
User Authentication: without cookies being sent to your browsing device, you might have to login every time you move from one webpage to another. This would be annoying, inconvenient and time-consuming. In the case of user authentication, cookies are extremely useful.
Identifying YOU: cookies can follow your preferences such as language or the preferences you express when on the website. Tailoring your preferences on this website can also be very useful.
Session Management: how and where you are on a website and anticipating your next move is also useful, especially on a large shopping site. Imagine if while shopping on Amazon, your shopping cart was not remembered as you continue looking for more stuff to buy. It would be not annoying but infuriating to have to keep putting those items back into your shopping cart. So far, so good.
Tracking and Analytics: websites track your movement through the website and begin to identify visitor preferences that will begin to match your likes/dislikes to advertisers on the website. Haven’t you seen an increase in emails and ads on other websites that seem to know you were looking for a Ring Doorbell because you are now getting similar offers for video equipment every time you open your Inbox or surf other shopping sites. How did they know that? Cookies.
Advertising: targeted advertising is created based on you, not magic. The Internet is vast, all-encompassing in our lives, and it seems to know you. Actually, the mass of computers that composes the Internet are simply reflecting your behavior as you surf around each day. You can always tell where the cookies were installed if you remember when you last were looking at home air conditioners – because suddenly, there is an increase in air conditioner offers in emails and the sidebar advertising when you go to Facebook.
When Cookies Become a Concern
Cookies are often designed to track your behavior across multiple websites because they have been placed by third party players on a website. If a website you visit monetizes their site with ads, those advertisers will place a cookie on your browsing device and the advertisers own computer systems will search the Internet looking for their cookies and when found, Level Two advertising efforts come into play.
Data Breaches – if a compromised cookie is placed on your computer, it can open the door to attacks on your computer exposing your personal data for malevolent use. This could be your login credentials or personal information that can be used to steal your identity.

Security Vulnerabilities – cookies placed on your computer may not be written in a way that is secure, and they can be exploited by bad actors on the dark web. Cookies often contain session identifiers or other sensitive information which allows unauthorized access to cookies by people not intended to have that information. This can cause endless problems, including privacy issues, malware attacks known as Cross-site scripting (XSS)) attacks which allow the injection of malicious client-side code (code inside your device), Cross-site request forgery (CSRF) attacks which mimic or impersonate a trusted user (such as your bank or credit card company), and more.

Managing Cookies
Browsers allow you to view, remove and block cookies. How that occurs depends on the device and the browser you are using. The convenience of cookies is obvious but the risks of never clearing your cookies is also apparent.
There are also many privacy tools that attach themselves and are known as Extensions to your browser. You will have to configure the extension to manage cookies the way you want – from very stringent to looser when managing cookies.
There is also scanning software that removes adware or suspicious cookies from your browser. If the cookie (remember it is a small text file uploaded to your computer) is malicious, simply deleting your cookies may not be enough.
Another option to consider is using a Virtual Private Network (VPN). This service will protect your internet connection and while it has a cost, it will give you considerably more protection than without.
To find information, Google: “Browser Extensions”, “VPN”, “Malware Removal” “Managing Cookies.” Do some research. It will pay off in the safety and privacy protection.
Looking for more? Read Chesa’s informative articles about Internet scams
- Introducing our Escaping Scams Series
- Escaping Scams #2 — Email is not always your friend
- Escaping Scams #3 — Tech Support Scam
- Escaping Scams #4 — Credit Card Reader Scams
- Escaping Scams #5 — Why We Get Scammed
- Escaping Scams #6 — If It Seems Too Good To Be True
- Escaping Scams #7 – Spoofing
- Escaping Scams #8 — The Heart Can Lie (Catfishing)

