Chesa Keane, an Associate member of Global Travelers, is a long-time consultant in many aspects of IT. As members of a virtual Rotary club, we are all, by definition, on-line to various degrees. And, like many things in life, being on-line comes with risk. Chesa has generously agreed to create a web series for our members with tips for helping us avoid becoming the victim of online scams. This is her seventh installment, focused on spoofing.
Scammers can trick you into thinking that the phone number or email address they give you is real. On your phone you see a phone number that seems real – it may even be a real phone number published on your bank or credit card website. During the process of the scam, you may even end up talking to the scammer and not only will they give you a spoofed phone number, but they will also take you through the validation steps you would expect the bank to use to verify that you are the customer. Imagine – you are proving to them – the scammer – that you are real. It seems safe and correct when they ask you for your PIN, your social security number, your address, etc. By then you have provided this valuable information, and you have given them the beginning of the bigger grift – stolen identification.

Just like phone numbers and email addresses can be spoofed, entire websites, emails and texts can be created by the scammer that look very, very real. They create these communications by using the same logos and communication styles of reputable businesses, banks and credit card companies. But look closely – there will usually be some mistake that a real company would not make. There may be grammatical or spelling errors that you would not expect from a reputable company.
How do you protect yourself from these intrusions? First of all, how did your engagement with them begin? Did you get on alert on your phone or by text message or by email? Generally, the initial contact scared you and can cause you to drop into their script, leading you along until you have given them too much information. What might be enough to scare you? A large Warning Notice across your computer screen that your computer has been infected with a dangerous virus. Or it may be an emailed invoice for $500, $1,200, $2500 or enough to make you concerned that someone has stolen your credit card or bank account. Maybe it’s a text or email threatening to expose you with fake videos/photographs they will post online if you don’t send them $10,000 in cybercurrency immediately. The threats are always strong enough to make it difficult to ignore.
Next, you need to learn how to ignore these threats. For most people, this is not easy to do. After all, you have been threatened. What is our first response? Stop the threat, fight back. That is natural, but you need to take a breath, step back and ignore the threat. Start by checking the source of the communication. For example, if you have received an email like this from Capital One, look closely.
You know you didn’t make a purchase for $1,200.50 because you would remember this purchase. But the colors are the same as Capital One would use and they are trying to help, right? No. First, the color scheme is an example of Spoofing. Just colors.
But what is more important, look at the email address from the sender. The address to me is correct, buy why isn’t the email address from Capital One a company address? Because it’s a fake, a scam.
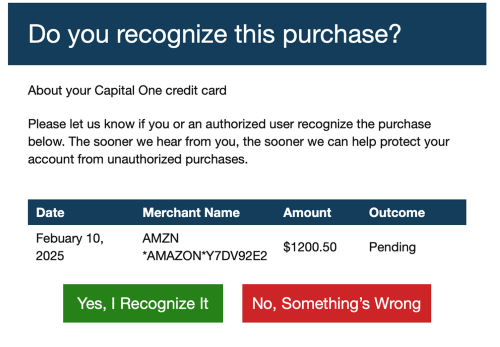


Never, never take their offer of help. If you click on the red button, No, Something’s Wrong, you will be taken to a location where the scammer will get all they need from you. You will be asked to call a number (spoofed probably) or provide via a form your personal information. And the validation process begins where you give them all the information, they need to clean out your bank account or charge your credit card to the max.
Don’t do it. Take a breath and ignore this email. If you are truly concerned, go directly to the bank, credit card or purchasing site to correct the problem. They will tell you that you are about to scammed and just delete the email.
It is not easy to ignore these threats, but by ignoring them, you will be safer. If need be, you can contact the company directly to straighten out the details. You must maintain control, or the scammer will be take advantage of you.
Be smart. Be safe.
Looking for more? Read Chesa’s other informative articles:

CONTACT US
Keep in touch, or reach out to us on social media!
All materials and photos, unless otherwise specified, copyright of Rotary E-Club Global Travelers.
All Rotary marks, logos, and copyrighted content are owned by Rotary International, used with permission.
Page design and upkeep: ADMarketing